analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
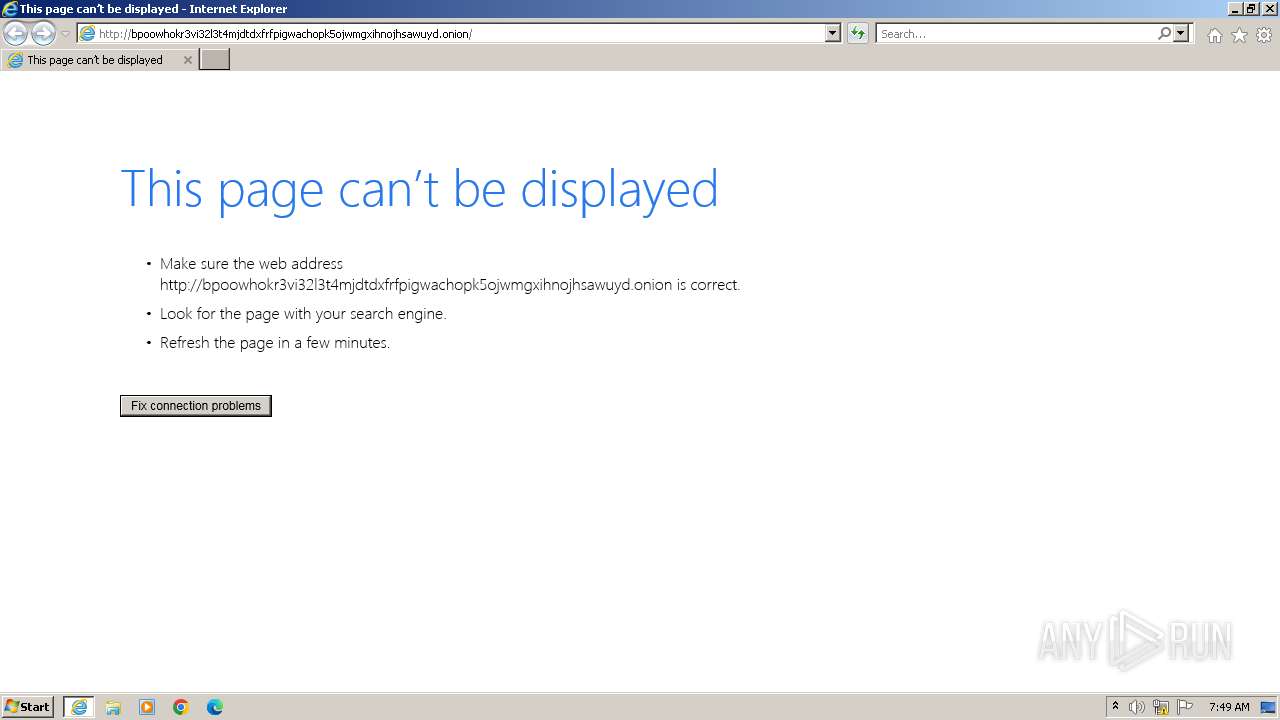
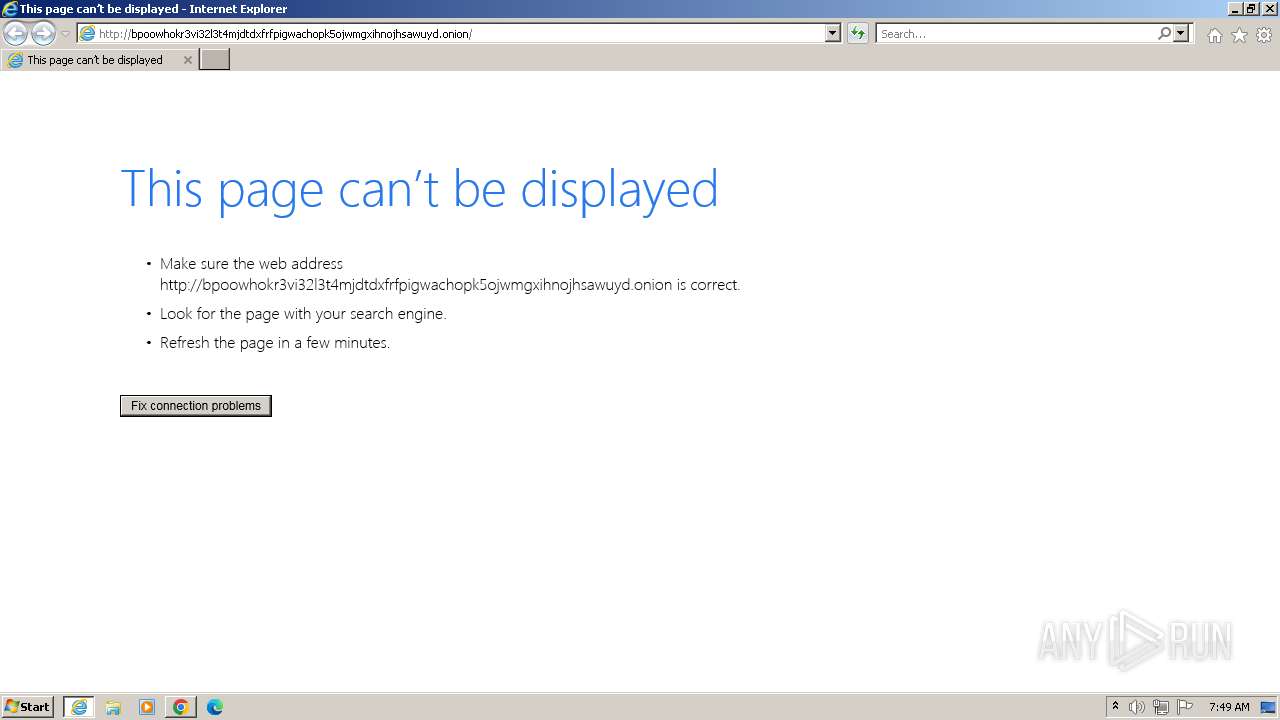
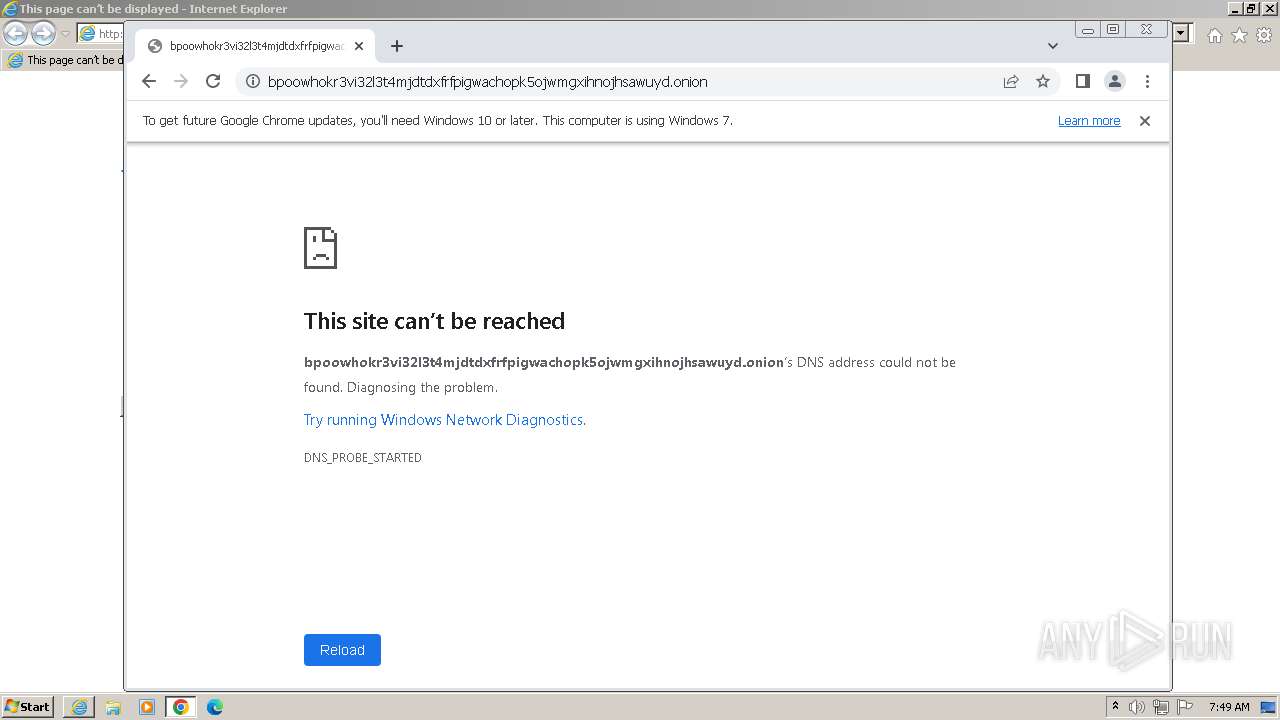
| URL: | http://bpoowhokr3vi32l3t4mjdtdxfrfpigwachopk5ojwmgxihnojhsawuyd.onion/ |
| Full analysis: | https://app.any.run/tasks/8622b9d6-fc9a-4f08-a659-230c6c680bdd |
| Verdict: | Malicious activity |
| Analysis date: | December 08, 2023, 07:49:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 85EFF45494257E02E309869928040257 |
| SHA1: | 609774072A1F6D8869C6B426CE5FF17213EBC51D |
| SHA256: | 5D43806205896F9AA9BC538F0F07686A5EDB0DC6B7DDDC6A460EF3D865588F35 |
| SSDEEP: | 3:N1Kc2I5hDfV/TdMZKYPLK4fn:Cc5NVrdKKYP+en |
MALICIOUS
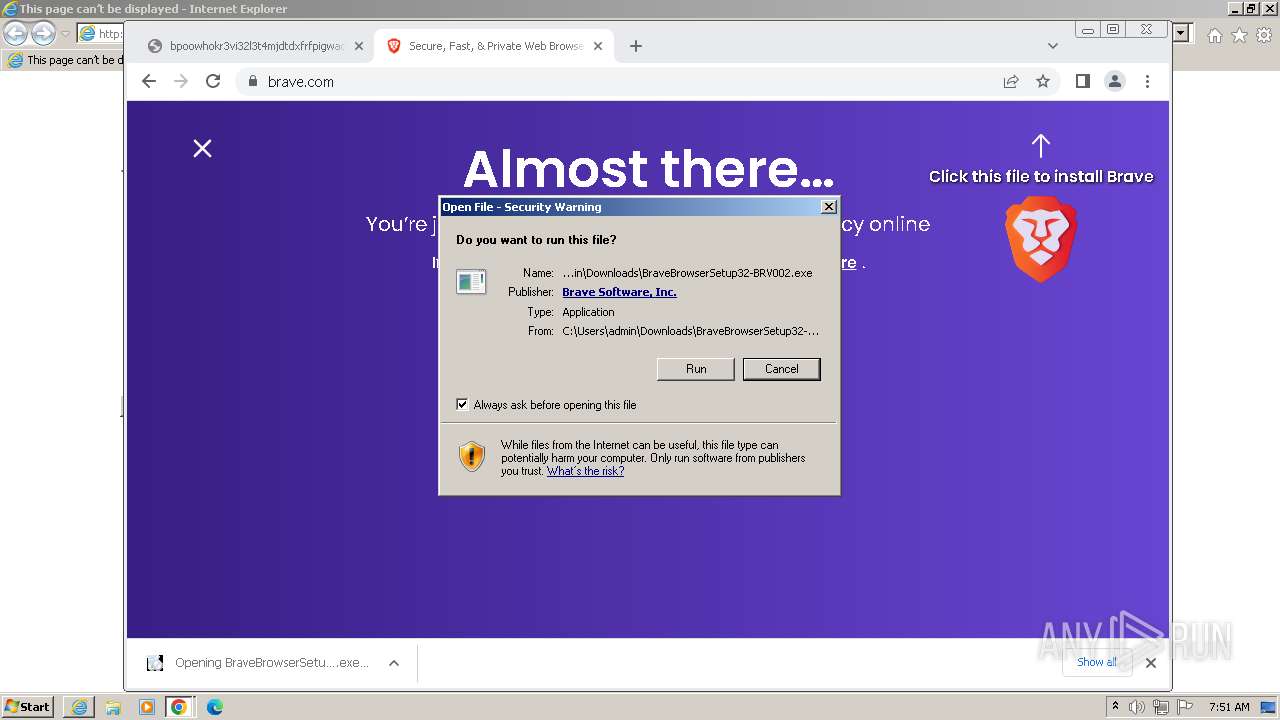
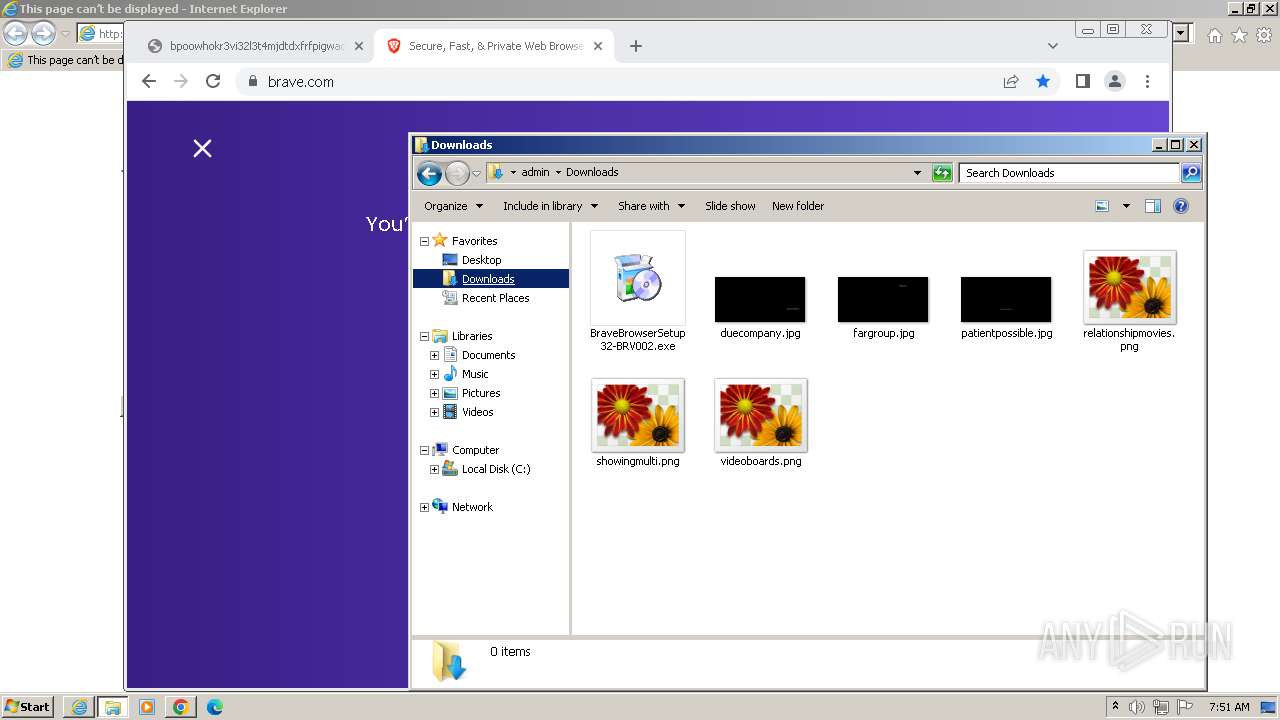
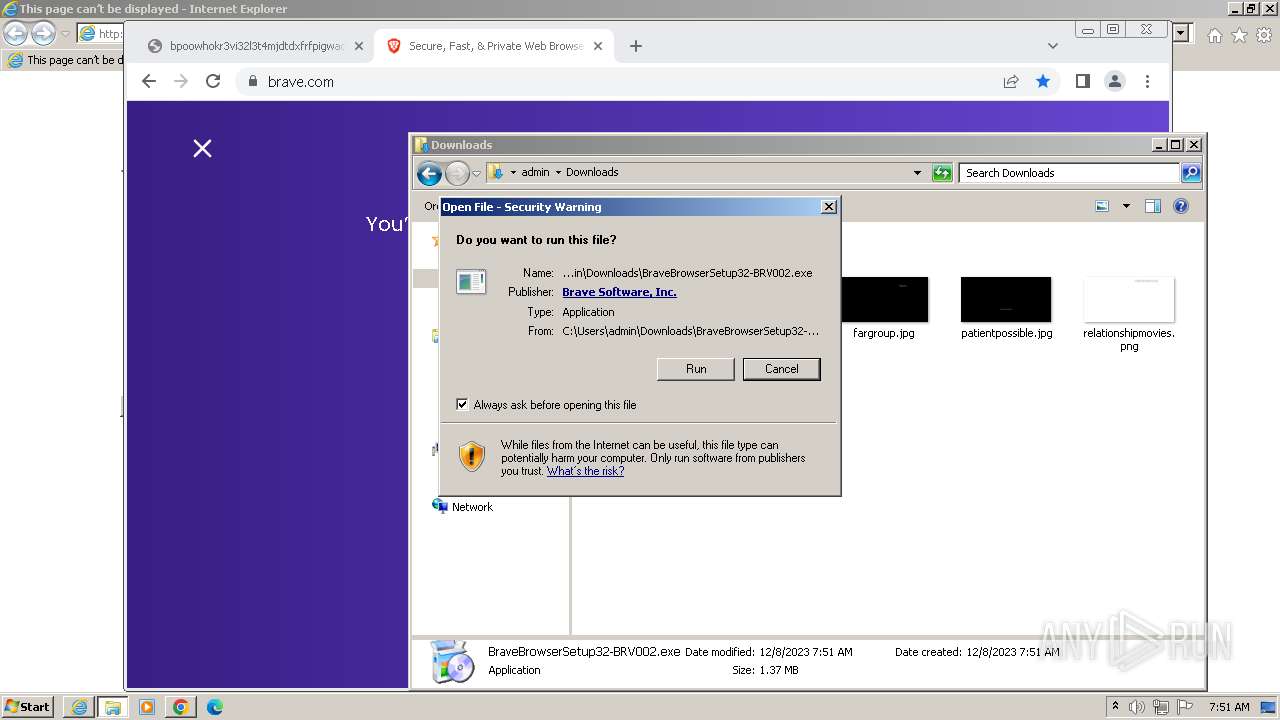
Drops the executable file immediately after the start
- BraveBrowserSetup32-BRV002.exe (PID: 2944)
- BraveUpdateSetup.exe (PID: 3808)
- BraveUpdate.exe (PID: 2296)
- BraveBrowserSetup32-BRV002.exe (PID: 2584)
- BraveUpdateSetup.exe (PID: 3408)
SUSPICIOUS
Process drops legitimate windows executable
- chrome.exe (PID: 2764)
Starts itself from another location
- BraveUpdate.exe (PID: 2296)
- BraveUpdate.exe (PID: 3500)
Creates/Modifies COM task schedule object
- BraveUpdate.exe (PID: 304)
Reads the Internet Settings
- BraveUpdate.exe (PID: 3436)
- BraveUpdate.exe (PID: 3696)
- BraveUpdate.exe (PID: 3860)
- BraveUpdate.exe (PID: 1816)
Executes as Windows Service
- BraveUpdate.exe (PID: 3212)
- BraveUpdate.exe (PID: 3560)
Application launched itself
- BraveUpdate.exe (PID: 3212)
- BraveUpdate.exe (PID: 3560)
Reads settings of System Certificates
- BraveUpdate.exe (PID: 3436)
- BraveUpdate.exe (PID: 3696)
- BraveUpdate.exe (PID: 3860)
- BraveUpdate.exe (PID: 1816)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 3812)
- BraveUpdate.exe (PID: 3292)
- BraveUpdate.exe (PID: 2296)
- BraveUpdate.exe (PID: 304)
- BraveUpdate.exe (PID: 2116)
- BraveUpdate.exe (PID: 3288)
- BraveUpdate.exe (PID: 3436)
- BraveUpdate.exe (PID: 3212)
- BraveUpdate.exe (PID: 3696)
- BraveUpdate.exe (PID: 2348)
- BraveUpdate.exe (PID: 3500)
- BraveUpdate.exe (PID: 1600)
- BraveUpdate.exe (PID: 3736)
- BraveUpdate.exe (PID: 3860)
- BraveUpdate.exe (PID: 3560)
- BraveUpdate.exe (PID: 1816)
Checks supported languages
- wmpnscfg.exe (PID: 3812)
- BraveUpdate.exe (PID: 3292)
- BraveBrowserSetup32-BRV002.exe (PID: 2944)
- BraveUpdateSetup.exe (PID: 3808)
- BraveUpdate.exe (PID: 3436)
- BraveUpdate.exe (PID: 2116)
- BraveUpdate.exe (PID: 3288)
- BraveUpdate.exe (PID: 2296)
- BraveUpdate.exe (PID: 304)
- BraveUpdate.exe (PID: 3212)
- BraveUpdate.exe (PID: 3696)
- BraveBrowserSetup32-BRV002.exe (PID: 2584)
- BraveUpdate.exe (PID: 2348)
- BraveUpdateSetup.exe (PID: 3408)
- BraveUpdate.exe (PID: 3736)
- BraveUpdate.exe (PID: 3500)
- BraveUpdate.exe (PID: 3860)
- BraveUpdate.exe (PID: 1600)
- BraveUpdate.exe (PID: 3560)
- BraveUpdate.exe (PID: 1816)
Application launched itself
- iexplore.exe (PID: 3264)
- chrome.exe (PID: 2764)
Manual execution by a user
- wmpnscfg.exe (PID: 3812)
- chrome.exe (PID: 2764)
- explorer.exe (PID: 2908)
- BraveBrowserSetup32-BRV002.exe (PID: 2584)
Drops the executable file immediately after the start
- chrome.exe (PID: 3564)
- chrome.exe (PID: 2764)
Reads the machine GUID from the registry
- BraveUpdate.exe (PID: 3292)
- BraveUpdate.exe (PID: 2296)
- BraveUpdate.exe (PID: 3212)
- BraveUpdate.exe (PID: 3288)
- BraveUpdate.exe (PID: 3436)
- BraveUpdate.exe (PID: 3696)
- BraveUpdate.exe (PID: 2348)
- BraveUpdate.exe (PID: 1600)
- BraveUpdate.exe (PID: 3500)
- BraveUpdate.exe (PID: 3560)
- BraveUpdate.exe (PID: 1816)
- BraveUpdate.exe (PID: 3860)
The process uses the downloaded file
- chrome.exe (PID: 2764)
- chrome.exe (PID: 4080)
- BraveBrowserSetup32-BRV002.exe (PID: 2944)
- BraveBrowserSetup32-BRV002.exe (PID: 2584)
Create files in a temporary directory
- BraveBrowserSetup32-BRV002.exe (PID: 2944)
- BraveBrowserSetup32-BRV002.exe (PID: 2584)
Creates files in the program directory
- BraveUpdate.exe (PID: 2296)
- BraveUpdateSetup.exe (PID: 3808)
- BraveUpdate.exe (PID: 3212)
- BraveUpdateSetup.exe (PID: 3408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
98
Monitored processes
52
Malicious processes
14
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3264 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://bpoowhokr3vi32l3t4mjdtdxfrfpigwachopk5ojwmgxihnojhsawuyd.onion/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2132 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3264 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2764 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 3140 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x688b8b38,0x688b8b48,0x688b8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1012 --field-trial-handle=1236,i,5926104738291434910,9247182555415756747,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 3564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1452 --field-trial-handle=1236,i,5926104738291434910,9247182555415756747,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 3916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1580 --field-trial-handle=1236,i,5926104738291434910,9247182555415756747,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 3600 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2128 --field-trial-handle=1236,i,5926104738291434910,9247182555415756747,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 4080 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2140 --field-trial-handle=1236,i,5926104738291434910,9247182555415756747,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 3536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1248 --field-trial-handle=1236,i,5926104738291434910,9247182555415756747,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
37 241
Read events
36 944
Write events
274
Delete events
23
Modification events
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3264) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
367
Suspicious files
184
Text files
69
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2764 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF211443.TMP | — | |
MD5:— | SHA256:— | |||
| 2764 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2764 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old | text | |
MD5:05387A3C4FCF1F3B992FF9FBF045AA1A | SHA256:B01E9451B8F6ABF03C9CD2E158C02D0A6BFDF771944F5D0B96DAD2DA6A7E3C8F | |||
| 2764 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF211443.TMP | text | |
MD5:E91E138A25FD7E5BCA5E60111F39C91A | SHA256:B1F7E3537A31A4B847F862858E5D2581993CC9372F19ABF19EA2A9185FE42A4F | |||
| 2764 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\839d641a-a2fe-4d6b-8252-d2fba6912fa0.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:CDB4EE2AEA69CC6A83331BBE96DC2CAA9A299D21329EFB0336FC02A82E1839A8 | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:8661E4080EE8CBB4F2BAE45EB5269C86 | SHA256:8E05CE6E9885CCA95BA85403D898CB793B3DEAA9BA2FCF3111E0D114BDA37705 | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:71ECCEA08BE08B8A81024AA239EE6D9B | SHA256:B8370E369E43DD7D769DBB4AFAF6206BB5D8452ABBB0AA81AE955B7778C79D7F | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3264 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[1].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
56
DNS requests
65
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3264 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 312 b | unknown |
3264 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9c39c51ec95c49f5 | unknown | compressed | 4.66 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad6eob6nunr64xlqs3i7jpbbwlqa_20230923.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230923.567854667.14_all_ENUS500000_ace7f54yxy3vtmc2mjkr5yii7sta.crx3 | unknown | binary | 21.2 Kb | unknown |
3264 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
3264 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
3264 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?947160355facb38e | unknown | compressed | 4.66 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad6eob6nunr64xlqs3i7jpbbwlqa_20230923.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230923.567854667.14_all_ENUS500000_ace7f54yxy3vtmc2mjkr5yii7sta.crx3 | unknown | binary | 16.1 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad6eob6nunr64xlqs3i7jpbbwlqa_20230923.567854667.14/obedbbhbpmojnkanicioggnmelmoomoc_20230923.567854667.14_all_ENUS500000_ace7f54yxy3vtmc2mjkr5yii7sta.crx3 | unknown | binary | 5.88 Kb | unknown |
3264 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
3264 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3264 | iexplore.exe | 2.20.142.251:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3264 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2764 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3264 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3564 | chrome.exe | 172.217.16.131:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
3564 | chrome.exe | 74.125.133.84:443 | accounts.google.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
bpoowhokr3vi32l3t4mjdtdxfrfpigwachopk5ojwmgxihnojhsawuyd.onion |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potential Corporate Privacy Violation | AV POLICY DNS Query for .onion Domain Via TOR - Not Google |
1080 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
3564 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
3564 | chrome.exe | Potential Corporate Privacy Violation | AV POLICY DNS Query for .onion Domain Via TOR - Not Google |
3564 | chrome.exe | Potential Corporate Privacy Violation | AV POLICY DNS Query for .onion Domain Via TOR - Not Google |
3564 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
1080 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
1080 | svchost.exe | Potential Corporate Privacy Violation | AV POLICY DNS Query for .onion Domain Via TOR - Not Google |
3564 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
3564 | chrome.exe | Potential Corporate Privacy Violation | AV POLICY DNS Query for .onion Domain Via TOR - Not Google |